Hellcat, a novel ransomware group, has emerged in the cybercrime landscape in 2024, posing a significant threat to critical infrastructure, government bodies, educational institutions, and the energy sector. This sophisticated gang operates under a Ransomware-as-a-Service (RaaS) model, providing ransomware tools and infrastructure to affiliates in exchange for a share of illicit profits. Hellcat distinguishes itself through its deployment of double extortion tactics, suggesting a calculated psychological approach aimed at maximizing victim humiliation and public exposure. This article delves into notable activities attributed to Hellcat during November and December 2024, drawing from observations by Cato CTRL and corroborated by third-party intelligence. Organizations can significantly bolster their defenses against emerging threats like Hellcat by leveraging robust security platforms such as the Cato SASE Cloud Platform, designed to disrupt the ransomware attack lifecycle.
Hellcat Ransomware: Technical Deep Dive and Attack Analysis
Ransom Demands and Target Selection
The operational tempo of Hellcat ransomware escalated notably in November 2024, marked by a series of double extortion attacks. Remarkably, the group and its affiliates orchestrated three distinct attacks on a single day, November 14, 2024, demonstrating a coordinated and aggressive approach.
Schneider Electric SE Breach (November 2, 2024)
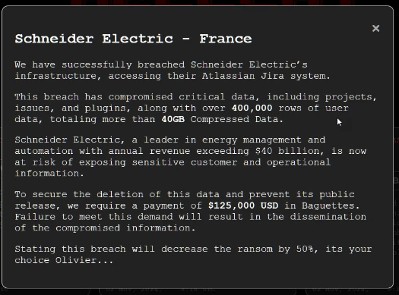
Figure 1. Schneider Electric SE Ransom Demand Displayed by Hellcat Ransomware Group
Incident Analysis: Hellcat successfully breached the internal Jira project management system of Schneider Electric SE, a prominent French energy corporation. The cybercriminals compromised an extensive dataset, encompassing 400,000 rows of user data and exfiltrating over 40GB of confidential information. The stolen data included sensitive details such as 75,000 unique email addresses and full names of Schneider Electric employees and clientele.
In a display of calculated mockery, Hellcat demanded a ransom of $125,000 USD, ironically denominated in “Baguettes,” highlighting a disturbing psychological tactic aimed at humiliating the victim organization. This emphasis on humiliation underscores a unique and concerning element of Hellcat’s operational methodology.
Cyberattack on Tanzania’s College of Business Education (November 4, 2024)
Figure 2. Hellcat Ransomware Group Data Leak Targeting Tanzania’s College of Business Education
Incident Analysis: In a collaborative effort with a threat actor known as “Hikkl-Chan,” Hellcat asserted responsibility for the exposure of over 500,000 records originating from Tanzania’s College of Business Education. The compromised data contained Personally Identifiable Information (PII) belonging to students, faculty, and staff. Notably, the “Hikkl-Chan” actor has been previously linked to the large-scale data breach affecting VKontakte (VK), a major Russian social networking platform, where sensitive data of over 390 million users was reportedly leaked. This connection suggests potential links or shared actors within the cybercriminal underworld.
Targeting a Major U.S. University (November 14, 2024)
Figure 3. Hellcat Ransomware Group Offers Root Access to U.S. University Server on Dark Web
Incident Analysis: Cato CTRL’s intelligence revealed Hellcat’s strategic shift towards a major U.S. university boasting annual revenues exceeding $5.6 billion USD. The ransomware group advertised root access to the university’s server for sale on dark web forums, priced at a relatively low $1,500 USD. Such unauthorized access could potentially jeopardize sensitive student records, critical financial systems, and essential operational data. The ramifications of such a breach include severe reputational damage, significant financial losses, and potential legal repercussions for the affected institution.
Breach of French Energy Distribution Company (December 1, 2024)
Figure 4. Hellcat Ransomware Group Listing Root Access for French Energy Distribution Company on Dark Web Marketplace
Incident Analysis: Cato CTRL’s investigations uncovered another attack targeting a French energy distribution company, with annual revenues surpassing $7 billion USD. Hellcat offered root access to this company’s server for a mere $500 USD. The consistent targeting of energy sector entities underscores Hellcat’s focus on critical infrastructure and their potential intent to disrupt essential services.
Cyberattack on Iraq City Government (December 1, 2024)
Figure 5. Hellcat Ransomware Group Advertises Root Access to Iraq City Government Servers on Dark Web
Incident Analysis: Hellcat expanded its target scope to government entities, advertising root access to the Iraq city government’s servers for a nominal $300 USD. This action explicitly signals their intention to disrupt essential public services. This incident is not isolated, as the Iraqi government has been previously targeted in cyberattacks. Notably, a prior supply chain attack resulted in the leak of a 21.58GB database containing voter data and PII from Iraq’s Independent High Electoral Commission (IHEC), highlighting the persistent cyber threats faced by Iraqi institutions.
Download the Q3 2024 Cato CTRL SASE Threat Report for more insights into emerging cyber threats
Hellcat Ransomware: Tactics, Techniques, and Procedures (TTPs)
Cato CTRL’s in-depth analysis has illuminated the specific tactics, techniques, and procedures (TTPs) employed by the Hellcat ransomware group:
- Exploitation of Zero-Day Vulnerabilities: Hellcat demonstrates a capability to exploit zero-day vulnerabilities in widely used enterprise tools, exemplified by their exploitation of Jira in the Schneider Electric SE attack. This highlights their sophistication and access to advanced exploit capabilities.
- Targeting Firewalls and Critical Infrastructure: The attacks against the U.S. university and the French energy distribution company reveal a deliberate strategy of targeting firewalls and critical infrastructure components. This suggests an understanding of network architecture and a focus on high-impact targets.
- Privilege Escalation: A consistent TTP is privilege escalation to gain root or administrator-level access within compromised systems. This level of access is crucial for deploying ransomware payloads and exfiltrating sensitive data effectively.
- Double Extortion: Hellcat employs double extortion tactics, a hallmark of modern ransomware operations. This involves not only encrypting target systems but also exfiltrating sensitive data prior to encryption. The threat to publicly release stolen data adds significant pressure on victims to comply with ransom demands.
Conclusion: The Escalating Threat of Hellcat Ransomware
The emergence of Hellcat in 2024 signifies a concerning evolution in the cybercrime landscape. By adopting a RaaS model and leveraging double extortion tactics, Hellcat is lowering the barrier to entry for ransomware operations and amplifying the psychological distress inflicted on victims. The group’s strategic focus on critical sectors such as government, education, and energy underscores the urgent need for organizations to fortify their cybersecurity defenses and maintain heightened vigilance against this nascent yet potent ransomware threat. Combating ransomware effectively necessitates continuous adaptation, proactive threat intelligence, and robust security measures to outpace these increasingly sophisticated cybercriminals.
Enhanced Protections Against Ransomware Threats
The Cato SASE Cloud Platform offers a comprehensive security architecture designed to disrupt the ransomware attack chain at every stage.
- Cato IPS (Intrusion Prevention System): Leveraging real-time threat intelligence feeds from diverse sources, Cato IPS proactively blocks potential ransomware activities, including:
- Preventing access to websites identified as likely sources of malware, ransomware command-and-control (C&C) infrastructure, and phishing attempts.
- Blocking communication with known malicious hosts attempting to propagate ransomware.
- Detecting and mitigating lateral traffic within the network that could be exploited by threat actors for ransomware deployment.
- Cato FWaaS (Firewall as a Service): Cato FWaaS enhances user protection by preventing access to malicious websites, particularly those categorized as malware distribution sites. This proactive web filtering minimizes the risk of accidental malware downloads that could introduce ransomware into the network.
- Cato NGAM (Next-Generation Anti-Malware): Cato NGAM provides an additional layer of defense, integrated with Cato ZTNA (Zero Trust Network Access). These advanced engines actively prevent malicious download attempts and block ransomware execution before it can compromise user devices, strengthening endpoint security.